GET YOUR DEFENSES READY

THE MOAT
Your first line of defense in the war on cyber-attacks.
ABOUT US
The Threat is Real…
According to the 2016 Cyberthreats Defense Report, 75.6% of organizations were breached last year. In fact, data breaches increased 40% in 2016, hitting an all-time high of 1,093. What’s more, the average cost of a data breach was $4 million!
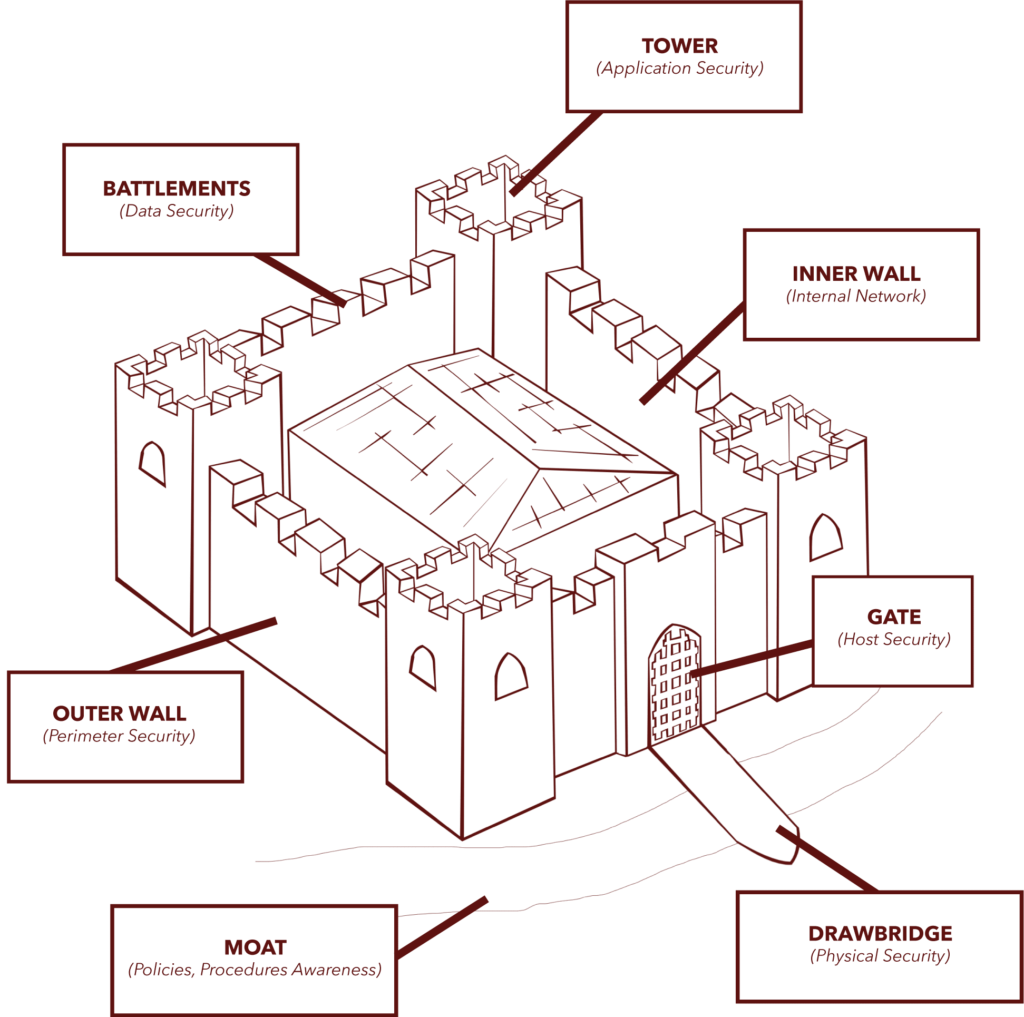
Roman Data Defense provides commercial organizations with multiple points of data security. Think of us as ethical, legal hackers who protect your business, technology and data, using both digital and physical security methods. If your business is your castle, we provide the fortress that guards some of your most valuable assets.
2,500+
Active Users
4,500+
Secured Devices
100,000+
Passwords
0
Data Breaches
WHO WE SERVICE
We provide data security to a wide range of clients, including commercial businesses, healthcare/medical offices, education, and financial services. Organizations, both small and large, are vulnerable to costly data breaches and can benefit from our comprehensive security services.
But, you don’t have to mortgage the castle to get the protection you need. Whether you have 10 personal devices or 10,000 computers, we can help you find the level of service that best fits your needs, from “build it and forget it” systems, to monitored security solutions.
Our Process
--------------------------------------- 1st STEP ---------------------------------------
SCOUT
We start by evaluating your cyber/data security strength: Where are the vulnerabilities in your systems? Are there warning signs of an attack? If so, is it one person or a whole army storming the castle? The objective is to find the gaps in the front line before the enemy does. The number of items we evaluate depends on the size and scope of your network: Basic and/or Advanced evaluations for smaller networks, and comprehensive evaluations for multi-site, complex networks. Based on our assessment, we decide whether to attack or defend.
--------------------------------------- 2nd STEP ---------------------------------------
ATTACK
If we find a threat, we charge! The objective here is to gain entry or disrupt business services. This type of attack can come from two fronts: external or internal. With an externally facing threat (think Russian hackers), we simulate what an attack from outside your network would entail. An internally facing threat is similar to corporate espionage (think angry employee), and involves protecting items such as accounting and employee records.
--------------------------------------- 3rd STEP ---------------------------------------
DEFEND
Great, you survived! If data has already been compromised, we offer a threat remediation service, evaluating the scope of the breach and correcting the security issue.
