Our Philosophy
Data is an essential part of any organization. Evolving security threats have forced companies to give special consideration to preventing data loss and monitor its flow throughout the organization.
Roman Data Defense provides commercial organizations with multiple points of data security. Think of us as ethical, legal hackers who use digital and physical methods to protect your business, technology, and data throughout its entire lifecycle. Our security solutions help organizations create a steadfast strategy to achieve the maximum protection against data breaches. Your business is your castle; we provide the fortress that guards some of your most valuable assets.
Our Founder
Our founder and CEO, Brian J. Hernandez, has extensive experience working with government agencies, including the Army and Department of Defense, with regard to cyber security and the prevention of cyber terrorism. He began his technical career working for the local computer store; from there he was recruited by AT&T to supervise a large IT team, eventually using his knowledge and expertise to operate on his own. His work with the federal government as a defense contractor gave him security clearance at the highest level. (We provide more details, but only on a “need to know basis.”) Brian’s thorough knowledge in data security gives him perspective from both sides: how to hack into a system and how to defend against these attacks.
Our Process
- - - - - - - - - - - - - - - - - - - - - - - - 1st STEP - - - - - - - - - - - - - - - - - - - - - - - -
SCOUT
We start by evaluating your cyber/data security strength: Where are the vulnerabilities in your systems? Are there warning signs of an attack? If so, is it one person or a whole army storming the castle? The objective is to find the gaps in the front line before the enemy does. The number of items we evaluate depends on the size and scope of your network: Basic and/or Advanced evaluations for smaller networks, and comprehensive evaluations for multi-site, complex networks. Based on our assessment, we decide whether to attack or defend.
- - - - - - - - - - - - - - - - - - - - - - - - 2nd STEP - - - - - - - - - - - - - - - - - - - - - - - -
ATTACK
If we find a threat, we charge! The objective here is to gain entry or disrupt business services. This type of attack can come from two fronts: external or internal. With an externally facing threat (think Russian hackers), we simulate what an attack from outside your network would entail. An internally facing threat is similar to corporate espionage (think angry employee), and involves protecting items such as accounting and employee records.
- - - - - - - - - - - - - - - - - - - - - - - - 3rd STEP - - - - - - - - - - - - - - - - - - - - - - - -
DEFEND
Great, you survived! If data has already been compromised, we offer a threat remediation service, evaluating the scope of the breach and correcting the security issue.
When it comes to data security, the cycle is continuous – scout, then attack or defend, and repeat. We protect networks on all fronts through training, teamwork and technology.
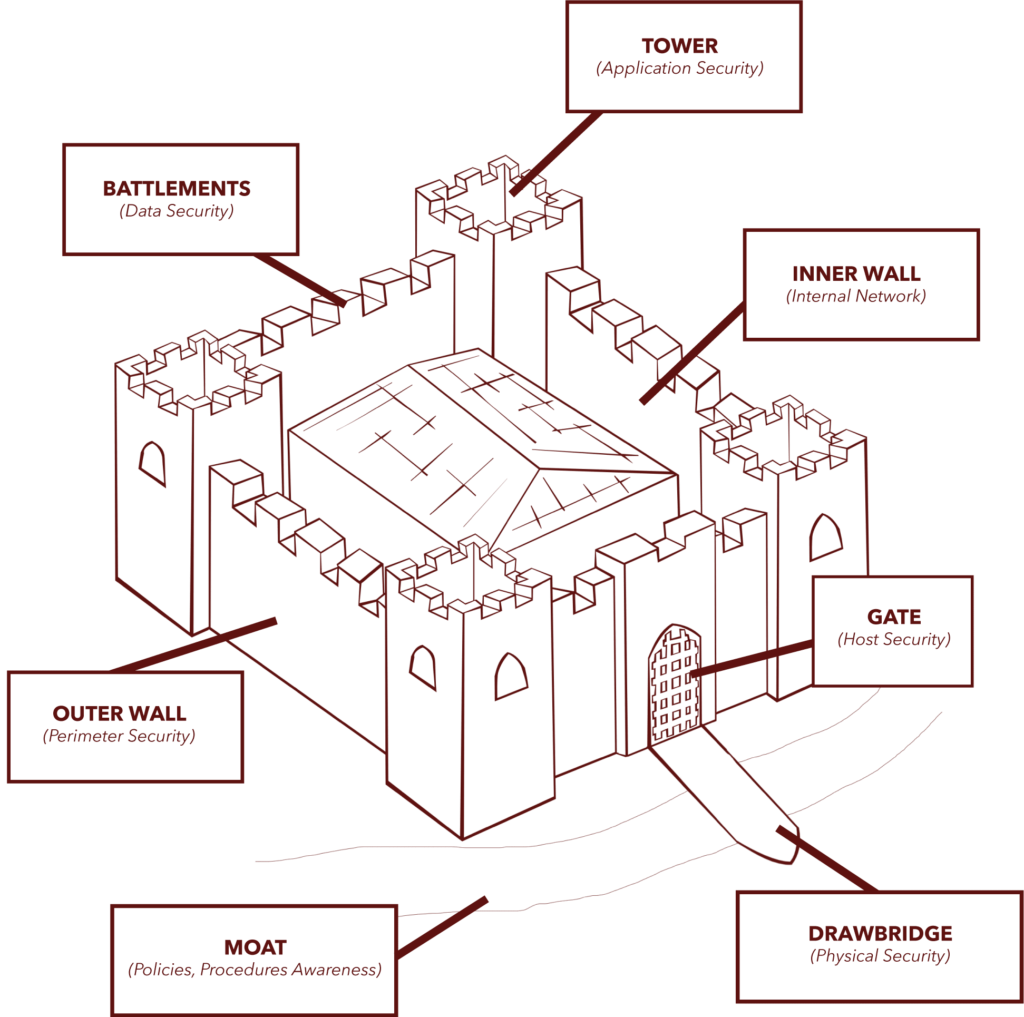
Several layers of cyber security exist, like a castle — both of which, if penetrated, create numerous access points to attackers. Choosing to include multiple layers in your network security ensures that each defense component has a backup in the case of a failing or missed scope. Each layer in a multi-layered security approach focuses on a specific area where the malware could attack. By working simultaneously, these layers of security have a better chance of stopping attackers from accessing company networks (your castle) than using a single solution.
