Are You Protected From Ransomware?
Ransomware is one of the most dangerous, prolific, and difficult viruses to deal with once you've already been attacked. It's not a matter of remediation because remediation means paying unknown sums of money to a hacker organization that never guarantees it won't just turn around and attack you again. It's a matter of protection.
Here's how it works.
The 3 Stages of Ransomware
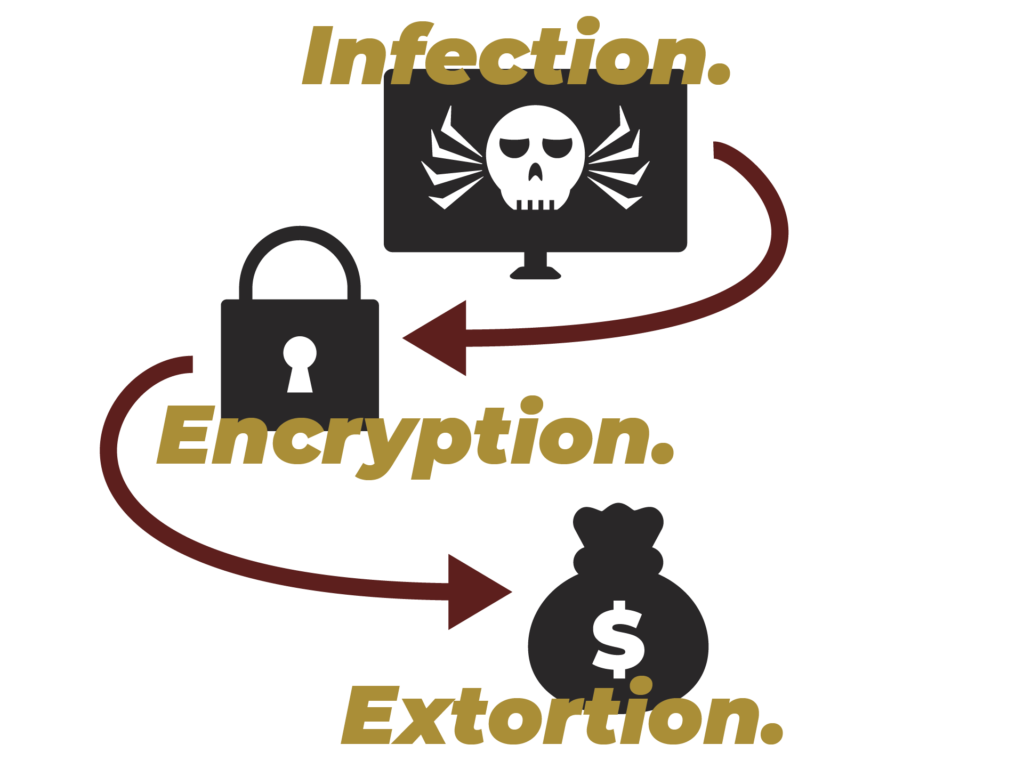
Infection
Your computer can get infected in quite a few ways. Some of the most common are by visiting suspicious websites or opening malicious attachments sent by people you don't know.
Encryption
The virus encrypts (locks) all of your files so you don't have access to them. Attackers usually leave one accessible file that states how you can pay the ransom.
Extortion
Attackers demand a ransom in exchange for a key that will unlock your files. The ransom is usually paid in a crypto-currency, like Bitcoin. Without paying the ransom, it's almost impossible to get your files back.
What Can You Do?
Here are 10 simple ways you can stay safe
01
Regularly test and check your back up copies so you aren’t hit with accidental failure which can damage your files.
02
Fine tune your anti-spam setting and don’t open attachments sent by an unknown sender. Cybercriminals will often send fake emails mimicking notifications from a store or bank to try to get users to click a malicious link.
03
Have the “Show file extensions” option enabled in your settings. Trojans are programs and can use extensions such as “exe”, “vbs”, and “scr”. You need a close watch since many familiar file types can be dangerous. Don’t install any program you don’t trust or didn’t deliberately download.
04
Keep your updates current. Attackers will exploit any weaknesses they can find in operation systems, browsers, and antiviruses to compromise systems.
05
Use an antivirus program to help protect your system. Some have capabilities to protect your important files if you end up being infected.
06
Install a browser add-on to block popups. Popups can serve as an entry point for ransom Trojan attacks.
07
Disable file sharing. If you happen to get hit, the ransomware infection will stay isolated to your machine.
08
Switch off unused wireless connections, like Bluetooth or infrared ports. Bluetooth connections can get exploited and stealthily compromise the machine.
09
If you discover an unknown process on your machine, disconnect from the internet immediately. If the ransomware didn’t erase the encryption key from your computer, you may still be able to restore your files.
10
If your files end up being encrypted, don’t pay the ransom unless you absolutely need instant access to your files. Each payment just encourages attackers and keeps the ransomware industry thriving.
